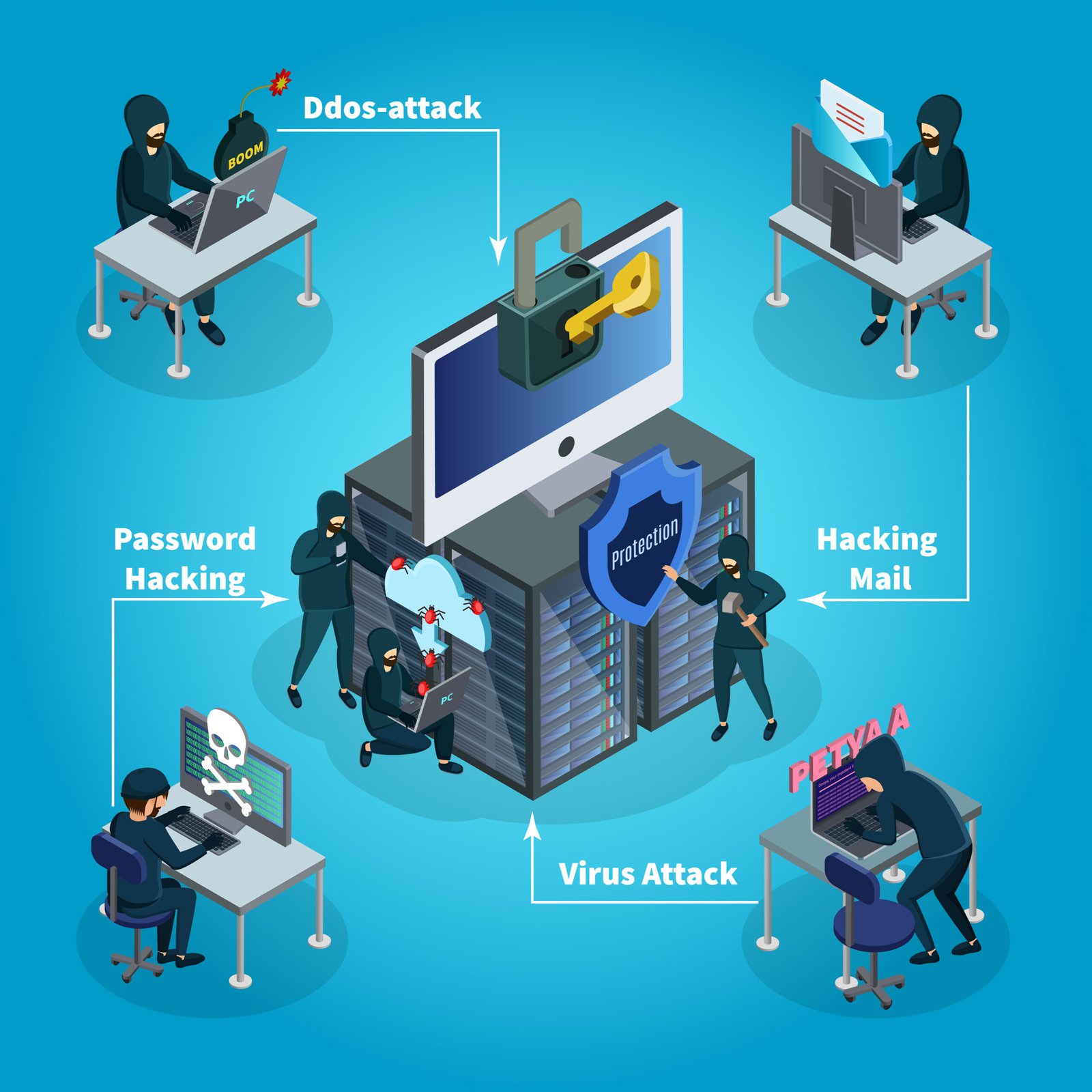
Did you know how cybercrime investigates digital data? In the vast expanse of the digital world, every action leaves an indelible mark, a digital footprint that can reveal hidden truths and unravel complex narratives. Cybercrime investigations of digital data have become a crucial tool in navigating this virtual landscape, shedding light on activities that span from routine transactions to cybercrime investigations.
Cybercrime Investigation with Digital Data
In today’s interconnected world, where the digital landscape dominates nearly every aspect of our lives, the rise of cybercrime has become a pervasive threat. From identity theft to financial fraud, cybercriminals are constantly evolving their tactics to exploit vulnerabilities in digital systems and networks. In combating these sophisticated threats, one crucial aspect is the examination of digital data—a process that unveils the intricate details behind cybercrime activities.
Understanding Cybercrime
Cybercrime encompasses a wide range of illicit activities conducted through digital means, such as hacking, phishing, malware distribution, and more. These criminal activities not only pose significant financial risks but also jeopardize individuals’ privacy and security. To effectively combat cybercrime, law enforcement agencies, cybersecurity professionals, and forensic analysts rely heavily on examining digital data to uncover evidence and trace the perpetrators.
The Role of Digital Data Examination in Cybercrime
Digital data examination plays a pivotal role in investigating cybercrime incidents and prosecuting offenders. Whether it’s analyzing network logs, examining email communications, or dissecting malware code, digital forensic experts employ various techniques and tools to extract valuable insights from electronic evidence. By scrutinizing digital data, investigators can reconstruct the sequence of events, identify potential perpetrators, and establish a chain of custody for evidentiary purposes.
How IT Solutions Revolutionize Collaboration and Communication
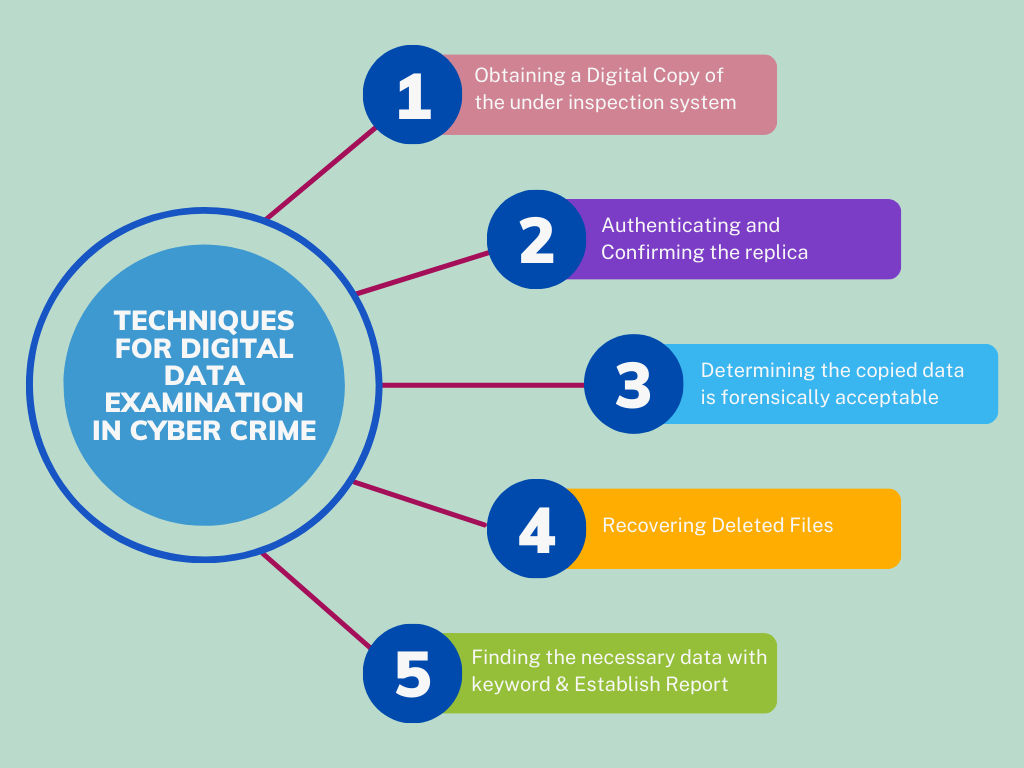
Techniques for Digital Data Examination
Forensic Imaging:
The first step in digital data examination involves creating a forensic image of the storage devices associated with the cybercrime incident. This process ensures the preservation of evidence without altering the original data, allowing forensic analysts to conduct thorough examinations while maintaining data integrity.
Keyword Analysis:
Keywords related to cybercrime, such as “phishing,” “malware,” or “data breach,” are instrumental in identifying relevant digital evidence. By conducting keyword analysis on seized devices or network traffic logs, investigators can pinpoint suspicious activities and focus their examination efforts on relevant data sources.
Metadata Analysis:
Metadata, which includes information about the creation, modification, and transmission of digital files, can provide valuable clues in cybercrime investigations. Forensic analysts meticulously examine metadata associated with documents, images, and other digital artifacts to establish timelines, track file movements, and attribute actions to specific individuals or devices.
Hashing and File Integrity Verification:
Hashing algorithms are utilized to generate unique identifiers, or hashes, for digital files. By comparing hashes of known files with those found on suspect devices, forensic analysts can detect unauthorized modifications or tampering attempts, ensuring the integrity of digital evidence.
Challenges in Digital Data Examination
Despite its critical importance, examining digital data for cybercrime investigations poses numerous challenges. The sheer volume of data generated in today’s digital ecosystem can overwhelm investigators, requiring advanced data processing and analysis techniques. Moreover, cybercriminals employ encryption, obfuscation, and other evasion tactics to conceal their activities, making it increasingly difficult to uncover incriminating evidence.
Understanding the need for Cybersecurity Outsourcing
The Future of Digital Data Examination
As cyber threats continue to evolve, the field of digital data examination must adapt and innovate to stay ahead of cybercriminals. Advances in artificial intelligence, machine learning, and blockchain technology hold promise for enhancing forensic analysis capabilities, enabling more efficient and effective detection of cybercrime activities.
Additionally, collaboration between the public and private sectors, along with international cooperation, is essential in combating cyber threats on a global scale.
Conclusion:
In the digital age, where data reigns supreme, the examination of digital footprints has become an indispensable tool in navigating the virtual realm. From recovering deleted files to decrypting encoded communications, digital forensic experts possess the skills and techniques necessary to unravel complex narratives, including those involving cybercrime.
However, the battle against those engaged in nefarious activities, including cybercrime, is an ever-evolving game of cat and mouse, requiring constant adaptation and innovation. As technology continues to advance, so too must the methods and tools employed by those tasked with safeguarding the digital realm.
Through collaborative efforts, information sharing, and the integration of cutting-edge technologies, the examination of digital data will remain a vital weapon in ensuring the security and trustworthiness of the virtual world, including in the ongoing fight against cybercrime.