Cybersecurity outsourcing refers to the practice of hiring third-party experts or organizations to manage and oversee an enterprise’s security protocols, systems, and infrastructure. This approach allows companies to leverage the specialized knowledge and skills of external cybersecurity professionals, often leading to enhanced protection against evolving cyber threats.
Here’s a comprehensive overview of cybersecurity outsourcing:
Understanding the Need for Cybersecurity Outsourcing
In an era fraught with sophisticated cyber threats, the need for robust defenses has never been more critical. Cybersecurity outsourcing offers a strategic solution for organizations to access specialized expertise and advanced technologies without the burden of maintaining an in-house team.
By leveraging external cyber security partners, businesses can bolster their security posture and stay ahead of evolving threats, ensuring comprehensive protection for their digital assets and sensitive information.
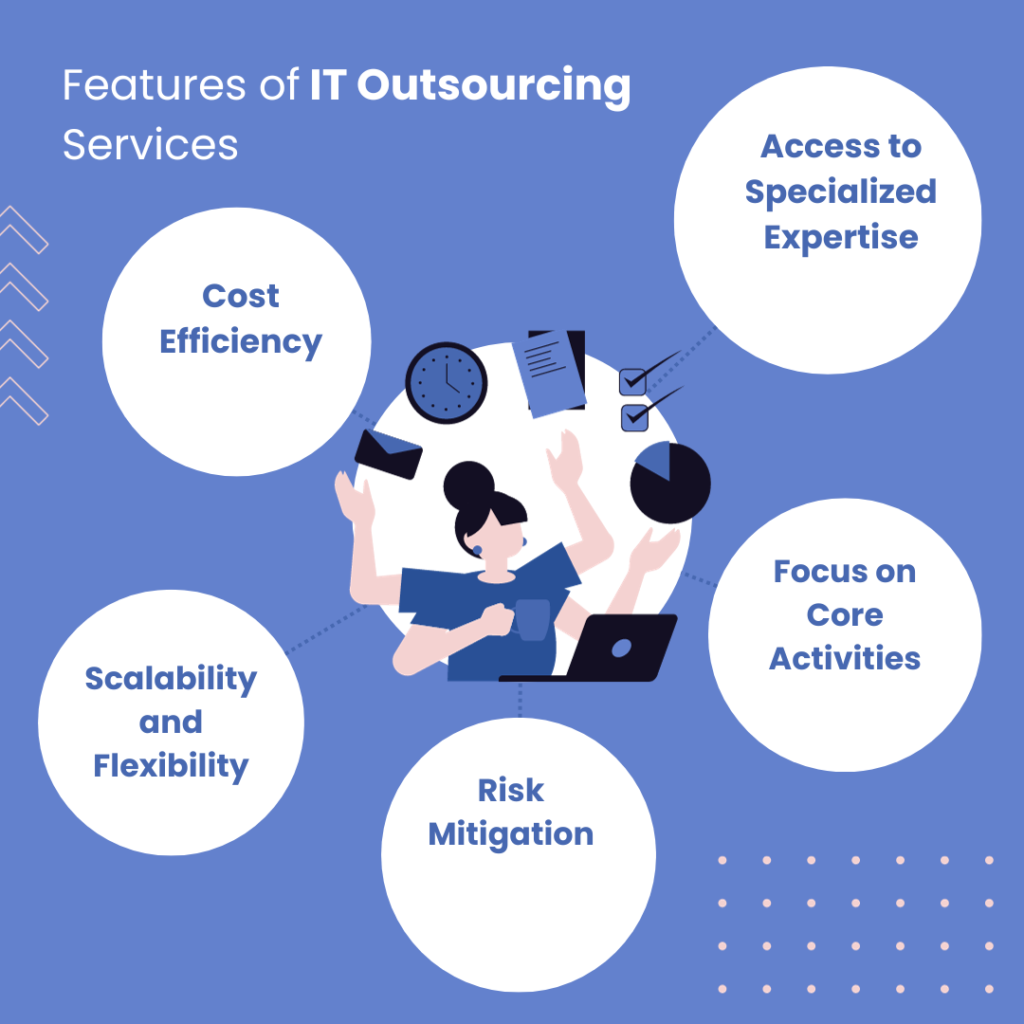
Benefits of Cybersecurity Outsourcing
Outsourcing cyber security can provide several advantages, including access to specialized expertise, cost-effectiveness compared to maintaining an in-house team, round-the-clock monitoring and support, the latest security technologies, and the ability to focus on core business functions.
Types of Cybersecurity Outsourcing Services
Managed Security Services (MSS)
Managed security service providers (MSSPs) offer ongoing monitoring, threat detection, incident response, and management of security systems.
Incident Response Services
These services focus on effectively handling and mitigating security incidents and breaches to minimize damage and ensure a swift recovery.
Security Consulting Services
Security consulting firms provide advisory services, risk assessments, compliance guidance, and security strategy development to help organizations strengthen their security posture.
Vulnerability Management Services
These services involve identifying and addressing potential vulnerabilities within a company’s systems, applications, and networks to prevent security breaches.
Key Considerations for Outsourcing Cyber Security
Security and Compliance Standards
Ensure that the outsourcing provider adheres to industry-specific security standards and compliance regulations to protect sensitive data.
Service Level Agreements (SLAs)
Establish clear SLAs that outline the expected performance, response times, and incident resolution procedures to maintain accountability and transparency.
Data Protection and Privacy
Prioritize data protection and privacy by confirming that the outsourcing provider employs robust encryption, access controls, and data handling practices.
Communication and Collaboration
Foster open communication and collaboration between the internal team and the cyber security outsourcing provider to ensure a cohesive security strategy.
Risk Management Approach
Choose a provider that adopts a comprehensive risk management approach, including threat intelligence, risk assessment, and proactive security measures.
Challenges of Cybersecurity Outsourcing
While outsourcing cyber security can be beneficial, challenges such as potential communication gaps, data breaches, lack of control over security operations, and varying service quality may arise.
It’s crucial to address these challenges through effective contract management, regular performance reviews, and ongoing communication.
Future Trends in Cybersecurity Outsourcing
As the cyber security landscape evolves, outsourcing providers are expected to incorporate advanced technologies such as artificial intelligence (AI), machine learning (ML), and automation to enhance threat detection and response capabilities.
By understanding the nuances of cyber security outsourcing, businesses can make informed decisions about partnering with the right providers to strengthen their security posture and mitigate potential cyber risks.
Read also: Revolutionizing Digital Era Customer Assistance with AI-Driven Chatbot
Factors to Consider When Choosing a Cyber Security Partner
When selecting a cyber-security partner for outsourcing needs, several crucial factors demand consideration. Evaluate the provider’s experience, reputation, and adherence to industry standards, ensuring their capabilities align with your specific cyber security requirements.
Look for strong service level agreements (SLAs) and robust compliance measures to safeguard sensitive data and maintain regulatory adherence.
Effective communication channels and a proactive approach to collaboration are essential, fostering a seamless integration of cyber security outsourcing operations with your organization’s overall security strategy.
Standardised methods for outsourcing cyber security

Thorough Vendor Assessment
Conduct comprehensive background checks and evaluations of potential outsourcing cyber security partners to ensure their credibility and expertise.
Clear and detailed contracts
Establish clear and detailed contracts outlining the scope of services, responsibilities, performance expectations, and legal obligations to prevent misunderstandings.
Regular security audits
Conduct regular security audits to assess the effectiveness of the cyber security outsourcing measures and identify any potential vulnerabilities or gaps in security protocols.
Continuous Communication
Maintain open and transparent communication channels with the cyber security outsourcing team to facilitate the swift exchange of information and collaborative problem-solving.
Data Protection Compliance
Ensure that the cyber security outsourcing provider complies with all relevant data protection regulations and industry standards to safeguard sensitive information.
Training and skill enhancement
Encourage continuous training and skill enhancement programs for the cybersecurity outsourcing team, thereby ensuring they remain updated on the latest security threats and technologies.
Scenario-based Drills and Testing
Conduct scenario-based drills and testing exercises to assess the outsourced team’s preparedness and effectiveness in handling various cyber security incidents.
Regular Performance Reviews
Regularly conduct performance reviews to evaluate the outsourcing cybersecurity team’s effectiveness and make essential adjustments to enhance overall security measures.
Proactive Threat Intelligence Sharing
Cultivate a culture of proactive threat intelligence sharing between the in-house team and the outsourced cybersecurity experts, thus enabling the ability to stay ahead of emerging cyber threats.
Flexibility and Scalability
Ensure that the cyber security outsourcing services can be scaled according to the evolving needs of the organization and the changing cyber security landscape.
By adhering to these best practices, organizations can effectively manage and optimize their outsourcing cyber security operations, thereby enhancing their overall security posture and resilience against potential cyber threats.
Strengthen Your defenses with Expert IT Outsourcing Services
When considering outsourcing cyber security, it’s vital to choose a partner with a proven track record and a deep understanding of the IT landscape. They should align with your organization’s specific security needs and regulatory requirements, ensuring a seamless integration of their services.
Mitigating risks and ensuring compliance are paramount. Robust service level agreements (SLAs) should be in place to safeguard data and maintain adherence to industry standards and regulations.
In a world where data is the lifeblood of business operations, outsourcing cyber security is not just a trend but a strategic necessity. By selecting the right partner and following these best practices, you can ensure your IT outsourcing operations are fortified against the ever-evolving threat landscape.

